Don't let Cybercriminals Steal your CX
In the last few years, businesses have dramatically changed how they use technology. This use increase has also opened the door to a spike in Cybercrime. Are you working on a retail app, website, or customer-facing project? Then you need to know what you can do to keep Cybercriminals from stealing your data and your Customers away.
What Cybercriminals may be stealing from your Company
Trust
Sales
Brand Reputation
The Customer Experience is critical to every project, manager, and organization. What is the risk? And how can you make your product, project, or department more prepared?
As a Project Management and former Customer Services department head, I feel your pain. To help summarize what to watch for, I have gone down the rabbit hole of Cyber security and developed this resource-rich summary for you.
The pandemic has sped up digital transformation by 68%. The customer experience has been made more convenient than ever. However, this statistic has raised the threat of Cybercrime to your customers at the same time.
Companies have improved their customers' digital access by integrating systems, increasing ease of entry, and proiding a single access point. Creating a treasure trove of customer data for thieves.
Because of these changes and other pandemic-related disruptions, global ransomware attacks increased by 62% from 2019 to 2020. - PBS
The problem with cyberattacks is that it locks the users out of their data, allowing attackers to steal and sell it. This leads to many cybercrimes such as identity theft, account takeovers, financial losses. Providing you and your customer with their worst nightmares. These sorts of attacks can hurt a brand in its weakest spot, the customer experience related to data use. Due to this, a business can lose all of its revenue, reputation, and ability to grow and exist.
More than 86% of respondents stated that they were "not at all likely" or "not very likely" to do business with an organization that had suffered a data breach. - CSOnline
Start with Data Security in mind
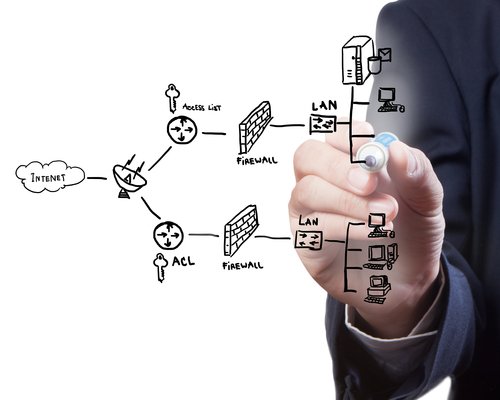
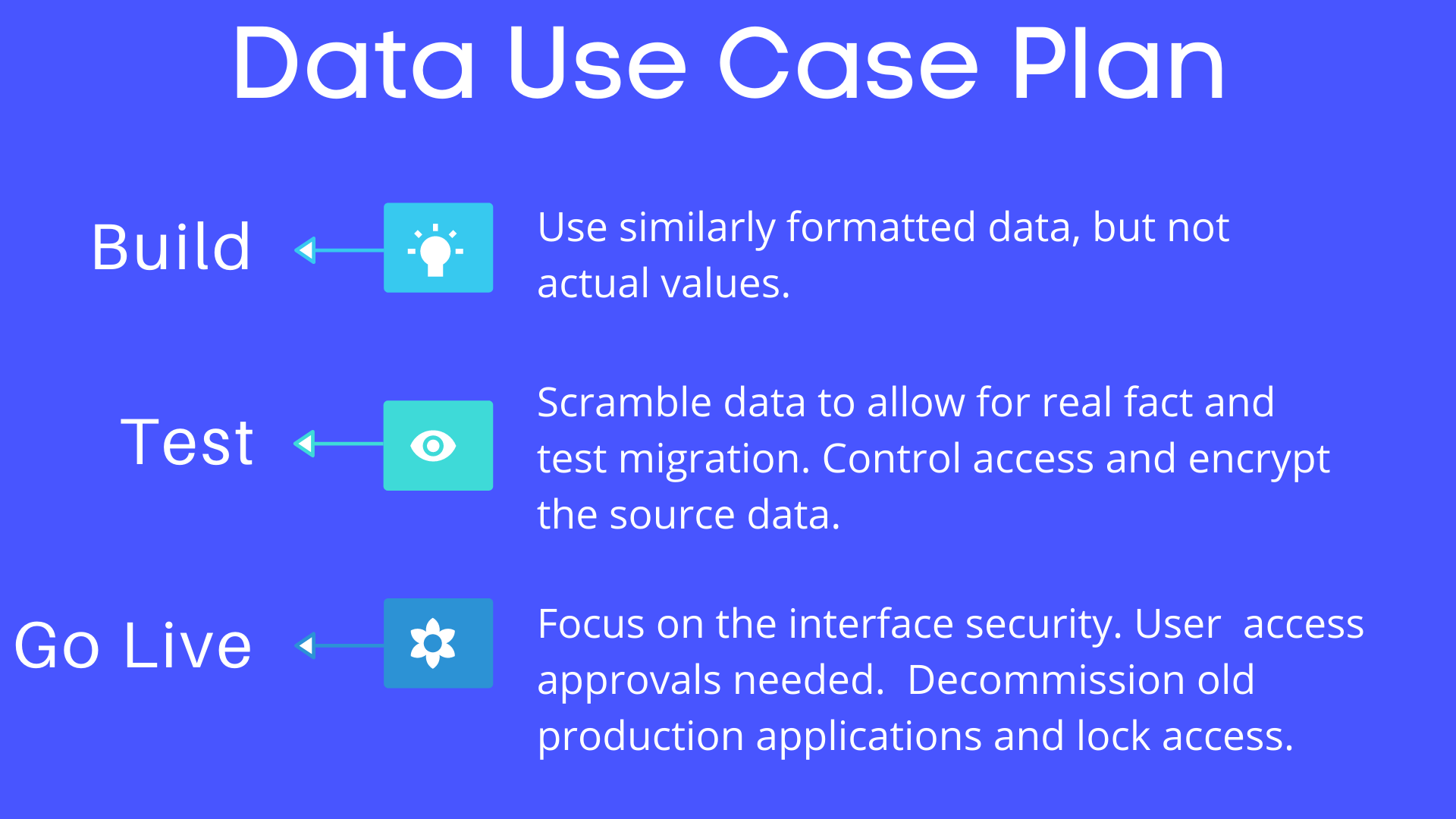
Start strong with security - put the process into every project. Create a data map documenting sources, uses, and interfaces to ensure no leaks are built during system development. Ensure the use case matches the data type and security plan. Every customer-facing or customer data-driven project should have a cybersecurity team working to protect the Customer Experience. Know what data you will use in each of the stages of the project. See the chart below for an example of this.
Businesses that invest time and effort into continuously making their cybersecurity stronger will avoid all sorts of disruptions in customer experience.
Let's review 3 best practices that can serve you, your projects, and your Customer.
Be Proactive
Companies and projects need to be vigilant. When an organization's data is breached, it also punches a hole through the consumer trust. Businesses must prove they can safeguard their customers - and show that they'll go the extra mile to beat Cybercrime.
Know the data you are collecting. For each attribute document the answers to these questions:
Do you have permission to access this data?
What is the use and storage policy?
What are the relevant data protection regulations?
What are the retention and archive plans?
When configuring systems, create a data map to ensure you understand how data is linked. Know what kind of data you have. Ensure that you know what is secured, unsecured, and how it can be accessed. Map the data flow to reduce the threat of access through unsecured sources.
Build your plan based on the regulations of your country or the countries where you do business—for example, GDPR for EU-based customers. The regulations may differ, but it is often best to take the most conservative approach when working in a global footprint. Be proactive with compliance to protect your customers from potential breaches and your Company from paying expensive fines.
Do you ask for only the information you need to authenticate them and provide a good experience? Are there data fields you could stop collecting without compromising fraud control and CX? If so, you can stop requesting that data going forward and securely purge the existing data. - CPO Magazine
Establish the right security protocols
Sustainable cyber security requires strong in-house policies. Focus on how you control and limit access to data, devices, and services. Follow industry standards such as:
Add 2 step user-identification.
Track and expose security risks during testing before updates are put into production.
Document system interfaces that can create failure points and open the door to hackers.
Evaluate your methods and update as needed based on these 10 points:
Set up automatic monitoring and flagging for suspicious traffic to and from your servers.
Encrypt data to a payment gateway, processor, fraud prevention, or any other partner.
Look for data exfiltration gaps in your system.
Create a playbook to allow your monitoring team to respond quickly when unexpected data movement is suspected
Strengthen your malware applications and firewalls.
Deploy site scanning to detect and remove any unknown entity that might lead to data-skimming attacks (which collect information from customers completing checkout forms).
Continuously review and update mail protection tactics. It can be hard to tell the real email from attacks. Use gate controls to protect your customer's data by ensuring those hacked emails do not reach their targets.
Track Customers' patterns of engagement and be on alert for changes.
Strengthen your customer identity and access management (known as CIAM). This can enhance security while simultaneously providing a premium customer experience.
Continuously review your cloud storage security to ensure that you aren't storing the data in a language easily comprehendible by humans. This situation has led to attacks on even big brands such as Facebook, Accenture, Verizon, and other companies.
According to a PwC report, 88% of customers' willingness to share personal information depends on how much they trust the Company. - PWC
Provide Consumer Data Transparency
Transparency helps to keep the trust of your customers. So share the details of your data policies and policing processes. This may deter attackers and help with customer confidence.
And, if your company has a breach, the response to that breach can determine to what extent the customer relationships will be damaged. Your brand reputation is at risk (quickly followed by a drop in sales, revenue, and stock value). So protect your Company by addressing the following if the worst happens:
Report it: let law enforcement and relevant regulatory bodies know the details.
Tell your Customers: be transparent. Tell them what you know, don't know, and what steps you will take to protect them.
Be Specific: tell customers what they need to do to protect themselves (such as changing their passwords or opting out of data collection and retention).
Follow up: stay in touch with customers post-breach with updates and, if needed, a special help-desk line.
Activate the Breach plan: Block access, check interfaces, run tests to look for exposure and malware.
Make it public: get the word out and take responsibility for the next steps. Send a signal to customers and stockholders that you have the situation under control.
Make a plan for various types of breaches to offer these monitoring services to the affected customers.
Most customers are ready to forgive a company if they know that the company is proactive and takes the right measures when needed. Your customers know that the hackers are out they, but they expect you to be ready. PWC calls this The Internet of Trust,
Start your cybersecurity protocols with every project that impacts key data, especially where customers are concerned. Invest in the right preparation, protocols, and transparency to make your brand as secure as possible. Create a 'culture of security and promote it - to your employees and customers. Trust can be hard to earn and very easy to lose, especially if it's customer trust. The best way to not lose it is not to let a breach happen.
What is the biggest issue with a project and customer security today? How do you plan to address data management on your project? Please let a note in the comments below.